Assuming you were tapped by the university president to evaluate the new enrollment system implemented this semester, enumerate your observations/comments and suggest possible areas and ways where improvements can be made. Your observations/suggestions should be properly validated with facts and literatures...(you may start with the diagrams posted in the strategic locations of the
university)...
It is now on its second year of implementation of the new enrollment system spearheaded by our department Institute of Computing. However, I must say that there are still some lapses and failures in terms of the SRMIS especially now that sometimes I was able to use the system. It was last summer S.Y. 2008-2009 when the new enrollment system was implemented. By the use of tarpaulins posted outside each department, the students are thoroughly guided.
With the non-IC students, they will not really pay attention to what kind of diagram use in illustrating the enrollment system, all that matters to them is that it will serve as steer for the enrollment. But until now, I could say that I’m still confused if they used a data flow diagram or a use case.
The New Enrollment System
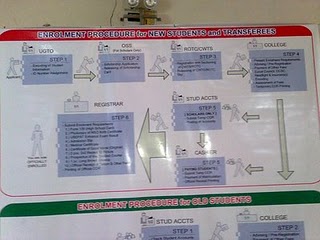
Enrollment Procedure for New students and Transferees
STEP 1 – UNIVERSITY GUIDANCE AND TESTING OFFICE
o Encoding of Student Information.
o Identification No. Assignment.
STEP 2 – OFFICE OF STUDENT SERVICES (Scholars Only)
o Scholarship Application.
o Releasing of Scholarship Card.
STEP 3 – ROTC/CWTS
o Registration and Sectioning of ROTC/CWTS.
o Releasing of ROTC/CWTS slip.
STEP 4 – COLLEGE
o Present enrollment requirements.
o Advising / Pre-Registration.
o Payment of other fees (Local Council fee, Obrero Campus Student Council fee, collegiate headlight fee and Insurance).
o Encoding.
o Assessment of fees.
o Temporary Certificate of Registration Printing.
STEP 5 – STUD ACCTS. (Scholars Only)
o Submit Temporary Certificate of Registration.
o Posting of Accounts.
STEP 5 – CASHIER (Paying Students)
o Submit Temporary Certificate of Registration.
o Payment of Matriculation.
o Official Receipt Printing.
STEP 6 – REGISTRAR
o Submit enrollment requirements.
Form 138 (High School Card).
Photocopy of NSO Birth Certificate.
USEPAT Entrance Exam Result.
Admission Slip.
Medical Certificate.
Certificate of Good Moral (Original).
2 pcs. 2x2 recent ID picture.
Prospectus of the enrolled course.
1 pc. Long brown envelop.
Official receipt of tuition and other fees.
o Printing of Official Certificate of Registration.
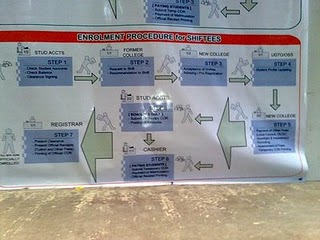
Enrollment Procedure for Shiftees
STEP 1 – STUD ACCTS.
o Check students’ accounts.
o Check balance.
o Clearance signing.
STEP 2 – FORMER COLLEGE
o Request to shift.
o Recommendation to shift.
STEP 3 – NEW COLLEGE
o Acceptance of Shiftee
o Advising / Pre- Registration.
STEP 4 – UNIVERSITY GUIDANC
E AND TESTING OFFICE / OFFICE OF STUDENT SERVICES
o Student Profile Updating
STEP 5 – NEW COLLEGE
o Payment of other fees (Local Council fee , Obrero Campus Student Council fee, Collegiate headlight fee and Insurance).
o Encoding.
o Assessment of fees.
o Temporary Certificate of Registration Printing.
STEP 6 – STUD ACCTS. (Scholars Only)
o Submit Temporary Certificate of Registration.
o Posting of Accounts.
STEP 6 – CASHIER (Paying Students)
o Submit Temporary Certificate of Registration.
o Payment of Matriculation.
o Official Receipt Printing.
STEP 7 – REGISTRAR
o Present Clearance.
o Present Official Receipts (Tuition and other fees).
o Printing of Official Certificate of Registration.
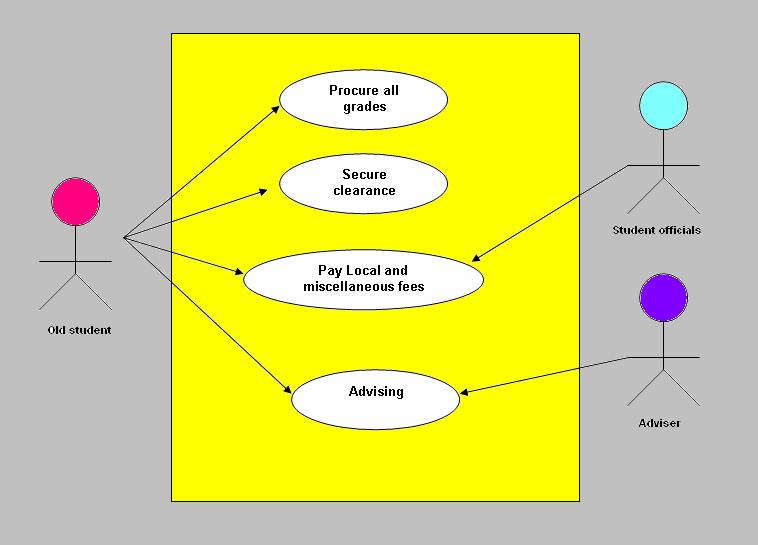
Enrollment Procedure for old students
STEP 1 – STUD ACCTS.
o Check students’ accounts.
o Check balance.
o Clearance signing.
STEP 2 – COLLEGE
o Advising / Pre- Registration
o Payment of other fees (Local
Council fee , Obrero Campus Student Council fee, Collegiate headlight fee and Insurance).
o Encoding.
o Assessment of fees.
o Temporary Certificate of Registration Printing.
STEP 3 – STUD ACCTS. (Scholars Only)
o Submit Temporary Certificate of Registration.
o Posting of Accounts.
STEP 3 – CASHIER (Paying Students)
o Submit Temporary Certificate of Registration.
o Payment of Matriculation.
o Official Receipt Printing.
STEP 4 – REGISTRAR
o Present Clearance.
o Present Official Receipts (Tuition and other fees).
o Printing of Official Certificate of Registration.
It is very noticeable that the sizes of the arrows hold opposing views that much. There are arrows that looks big which I think not so as to essential to look that way. There is also an arrow from student accounts which are applicable for scholars only pointing to cashier when in fact after the scholars submitted their temporary COR to the bookkeeper and have been checked they will go directly to the registrar.
If I were to say, the kind of arrows shown in the pictures above was not carefully thought before being posted. Maybe it was prepared well but there is no consistency with the diagrams just by looking with these small details. There are also small and big arrows pointing on the same direction which I think are better when it is drawn with definite size.
If I may add, in consideration for the scholars, if you will see the illustration I discerned that the scholarship card validation which takes place at the office of the student’s services was not in it. For the scholars like me, could not have our Pre- Registration form (PRF) encoded unless we can have our scholarship cards (Blue cards) validated. Well in fact, almost half of the students of the university are scholars and with this small disregard may cause some problems during enrollment.
In observation, the processes portrayed by the new enrollment system do not greatly differ to that of the old enrollment system. It has the same initial steps and same manner of dealing out with the transactions.
It was not like that during the previous enrollment system, the previous enrollment system had the encoders give you four copies of the COR, one copy is yours; the others are to be handed to the university bookkeeper and registrar’s office. But before after paying to the cashier (for the non-scholar), they will give the student two copies of the COR, one for the registrar and one for the student. But now, they will only receive a receipt for what they have paid and then they will be waiting for a very long queue of line of students for registration. I thought is they don’t really need a lot of documents any more since the database is now computerized and will be found on the server somewhat on the steel cabinets.
I think it was not that easy because as I have said awhile ago this time, the student will have to wait at the university registrar longer than you needed to since it takes a lot of time to print new sets of CORs. For Old students like us, I think these kinds of diagrams may be not that important at all. Old students from the university already know how the enrollment system in the university flows. Although the system was new, as for students nothing is new, we still doing the same as what we have always do during enrollment last semester. The students will just say that though they are the customers but still they are not the one operating the system so I don’t think that the tarpaulin was really needed.
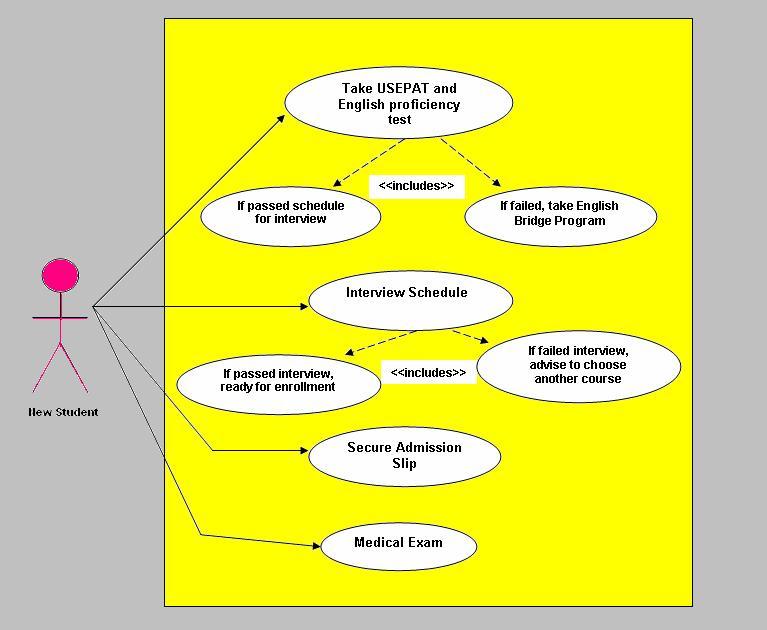
Taking the side for the new students or transferees, it is really a must to have an illustration but then again the illustration posted, I think was not that accurate enough at least for those transferees. Not all transferees have to take up ROTC/CWTS; they may have already taken it up on their previous school. Transferee’s needs to have their subjects taken from other school validated here if the course or subject description is the same so that he/she don’t have to take it all over again here.
Well, there is no big deal when it comes to the process because we all know as a student, we have to do all the procedures whether we like it or not. But for the convenience of the students, the University should hire or assign more personnel to accommodate a lot of students. The university should also provide electric fans around the cashier and registrar area. The area was too small; and should be relocated to a bigger area, more conducive for us students. These areas were too small for all the students from the seven colleges.
I suppose that there is still no major adjustment found in the system software that would affect to how the transactions are handled, the effectiveness of the system, and other factors. The speed to how the communications are processed still depends on the cooperation and how the people adopt the system.